FAQ about 2-factor authentication for staff
FAQ on the topic...
General questions
How do I set up 2-factor authentication?
For details on how to set up 2-factor authentication, please refer to the instructions published specifically for this purpose.
Which services are no longer accessible without 2FA activation??
After activation, all services protected by the so-called “Shibboleth login” are protected by another factor during authentication. These include
- KUS portal
- RRZ service portal
- Fiona
- UHHCloud
- VPN
- STiNE
In order to continue using these services, it is imperative that you follow the instructions published specifically for this purpose and act accordingly.
The protection of further services is being planned and will be continuously expanded.
Why does the service I want to sign up with not recognize that I have already registered my device?
If you regularly delete cookies (or the local storage) in your browser or use your browser in private mode, the information that your device is already registered cannot be saved.
How does 2FA work on public PCs at the university (in libraries or computer pools / labs)?
Public PCs cannot and should not be set up as 2FA devices. When working at a public PC, you have the following options for logging in:
- If you have already registered your smart phone for 2FA, you can use that. See instructions
- You can use a FIDO stick as a 2FA if you have one. See instructions
- You can use your 2FA code list as a 2FA.
Is it possible to use private devices for 2FA?
From a technical point of view, there is nothing to be said against the voluntary use of private end devices to register and use them as a second factor. The minimum requirements for the respective system specifications must be met here. These are named in the respective instructions for preparing the respective device class. Please understand that we cannot provide extended support for private devices.
How does 2FA work on PCs that are regularly used by different employees (shared workstations/devices)?
On devices managed by the RRZ, it is theoretically possible for several users to assign an individual Windows Hello pin to a (shared) device.
For security reasons, however, we strongly advise against using the Hello pin on such devices.
- You can use your smartphone as a second factor, provided you have registered it in advance. To the instructions
- You can use a FIDO stick as a second factor if you have one. To the instructions
- You can use your 2FA code list as a second factor.
2FA code list
What is a 2FA code list?
The personalized 2FA code list contains 240 codes and can be used as the second factor in a 2FA authentication. Using the list, you can also register further devices as 2FA.
Important: The 2FA code list validity is unlimited and non-transferable.
How do employees obtain a 2FA code list?
The list will be sent by mail to your postal address on file at UHH. The address data comes from the Digital Personnel Management.
I don't have the code list (anymore), what can I do?
To counteract problems such as a forgotten 2FA code list, it is advised to register multiple devices as a second factor. Please follow the corresponding instructions for this.
If you have not received a 2FA code list, please visit an RRZ-ServiceDesk (bring a valid photo ID).
In case you have lost your 2FA code list and you cannot issue yourself a new list because you have not yet registered a terminal device for two-factor authentication, please also visit an RRZ-ServiceDesk (bring valid photo ID).
If you are not able to visit an RRZ-ServiceDesk, please contact the RRZ-ServiceLine.
Can I create a new 2FA code list for myself?
If you suspect that someone else has spied out your 2FA code list or you have lost your list, you can create a new list for yourself. However, this is only possible if you have your own list, or if you have registered at least one other device as a second factor.
If the above requirements are met, create a new list after logging in on this page using the "Request new 2FA code list" item below.
Why should I not permanently use the code list for authentication?
While 2FA code slips can potentially be spied on or photographed by third parties without you noticing, 2FA devices are more secure as they would have to be physically stolen, which you would usually notice immediately. Please therefore prefer to use 2FA devices for increased security of your accounts. Also consider deactivating your 2FA code slip in the 2FA device registration if you do not need it.
Windows devices
What is Windows Hello?
Windows Hello is a more secure way to instantly access your Windows 10 devices using a PIN, facial recognition, or fingerprint. You also need to set up a PIN if you want to set up a fingerprint or facial recognition. Whether fingerprint and facial recognition are possible depends on the hardware you are using.
How can I set up Windows Hello?
See the instructions for the 2FA to set up Windows Hello.
Why can't I activate Windows Hello? I cannot activate the option.
If you are using a computer administered by the RRZ (a so-called FMD or Fully Managed Device) and are not on the premises of the UHH, it is necessary that you always establish the VPN connection before logging in to the computer. (Here you can find the instructions for VPN before Login (in German only).)
If problems persist, please contact the RRZ service line.(serviceline"AT"uni-hamburg.de?subject=2FA:%20FMD:%20Windows%20hello%20pin%20nicht%20aktivierbar).
How long should my Windows Hello PIN be?
You need at least 4 characters for the PIN. The more characters you use, the more difficult it is to guess the PIN. Windows does not accept obvious or easy PINs (e.g., 1234, 0000, 5678). The maximum character count for PINs is 127.
Isn't a Hello PIN more insecure than using the previous login (local authentication or network authentication)?
An important difference between an online password and a Windows Hello PIN is that the PIN is connected to the particular device on which it has been installed. Without this hardware, the PIN is useless for third parties. Someone who gets hold of your online password can log into your account from anywhere, but this person gets hold of your PIN, he or she must also have access to your device. The PIN can be used only on this device. If you want to log in to several devices, you need to install Hello on each of them.
PINs are saved locally on the device.
An online password is transmitted to the server. The password can be intercepted or recalled by the server. A PIN is transmitted locally to the device, never to a random place and never saved on the server. When the PIN has been created, it establishes a trustworthy connection to the identity provider and an asymmetric pair of keys that are used for authentication. When you type in your PIN, the authentication key that is used to sign the prompt is unlocked, and sent to the authentication server. Although local passwords for the device are local, they are less secure than a PIN, as described below. PINS are hardware-supported.
The Windows Hello PIN is supported by a Trusted Platform Module (TPM) chip. This is a secure cryptoprocessor that performs cryptographic procedures. The chip encompasses multiple physical security mechanisms that protect it from manipulation and malware cannot manipulate the TPM safety features. Windows does not connect local passwords with the TPM, which is why PINs are considered safer than local passwords.
User key material is generated and made available in the device’s TPM. The TPM protects the key material from attackers who want to record and reuse it. Because Windows Hello uses asymmetric key pairs, user log-in information cannot be stolen if the identity provider or the websites accessed by users have been compromised.
The TPM protects you from different well-known and potential attacks, including PIN brute-force attacks. The device will be blocked after too many erroneous attempts. PINS can be complex.
The Windows Hello for Business PIN is subject to the same statute of IT administrative bylaws as a password, e.g., with regard to complexity, length, expiry, and processing. Even if we normally envision a simple 4-character code for PINS, you can create more complex ones comparable to those of passwords. You can use the following characters: special characters, capitals, lower-cased, and numbers.
What do I do if I forget my Windows Hello PIN?
The Hello-PIN is merely an alternative login option for a specific computer and does not completely replace the password. If you no longer remember your Hello-PIN, you can reset it using your existing Windows 10 password.
Note:
After the Hello PIN has been changed, the device must be re-registered as a second factor, just like when the device was first registered.
The “Forgot PIN” button can be found in the “Login options” in the “Accounts” section in the “Settings” of the operating system.
- For devices of type “FMD” administered by the RRZ, the “Forgot PIN” option is only active if you have started VPN before the Windows login. Exactly as explained on the background image of the login screen. In addition, you must not have used the Hello PIN itself to log in to the device.
- For devices of the type “library computer” administered by the RRZ, the option “Forgot PIN” is only active if you are on the university campus and the device was started with a connected network cable and the Hello PIN itself was not used to log on to the device.
What is the difference between the Windows Hello PIN and my device password?
The Hello PIN is simply an alternative log-in option for a specific computer. It does not completely replace your password. If you cannot recall your Hello PIN, you can reset it using the existing Windows-10 password.
Do I need to set up a Windows Hello PIN?
No. Setting up the Windows Hello PIN facilitates authentication with a second factor, because the Hello PIN acts as a second factor. If you do not set up the Hello PIN, you will need to use another second factor (code combination from the 2FA code list, mobile device, FIDO2 stick) to log in to UHH services that require a second factor.
What happens to 2-factor authentication if I remove the Windows Hello PIN again?
The need to authenticate with a second factor is unaffected. If you do not set up the Hello PIN or remove it again, you will need to use another second factor (code combination from the 2FA code list, mobile device) to log in to UHH services that require a second factor.
Why do you need a PIN when using biometrics?
Windows Hello facilitates the biometric log-in for Windows: finger print or eye or facial recognition. If you set up Windows Hello, you will first be prompted to create a PIN. With this, you can continue to log in if you cannot use your preferred biometric data due to an injury, or the sensor not being available or functioning properly.
If you have configured only a biometric log-in but cannot use this method to log in for whatever reason, you have to log in with your account and password. This will not provide the same protection as Hello.
Why do I get an error message when I try to establish a VPN connection when using WIN11?
In a few cases, there is currently an error message when trying to establish a VPN connection and authenticate with a second factor for this purpose.
Error message:
Authentication failed due to problem navigation to the single sign-on URL
Solution:
Please set the Microsoft Edge browser as the default browser.
Why do I have a problem after using Hibernate with my Win10 device?
In a few cases, there is a problem with the 2FA when you restart your end device with a Windows 10 operating system.
After you have chosen “Authenticate using this device” and put in your PIN, you will be prompted to plug in a security key contained in a flash drive / memory stick.
If this happens, click “Cancel” to close the message, and then click “OK” in the new window to restart authentication. It should work this second time around.
Why am I suddenly no longer offered a Hello pin for authentication in Chrome / Edge?
Due to an update in Chrome and Edge, it may be that after you choose “authenticate using this device,” the Windows Hello PIN and/or other possible options are no longer offered in the window that opens.
In this window, choose:
- for Chrome— “Use external security keys” and
- for Edge— “Use an external security key.”
You will again receive the full range of options.
Apple devices
Error message: This request has been cancelled by the user
In a few cases you will receive the above error message on iPhone and iPad devices and it will not be possible to register them.
Currently, efforts are underway to find a solution.
What does “To secure a passkey, iCloud Keychain must be enabled” mean?
Apple synchronizes the second factor between all Apple devices with the same ID. So if you have registered your iPhone as second factor, automatically also e.g. your iPad or Safari is registered on the Mac - provided that the operating systems are up to date accordingly, see below.
To enable the synchronization of the second factor, the mentioned function must be activated. Apple does not allow usage without synchronization.
Requirement for the operating systems:
- iOS/iPadOS version 14.1 or higher
- macOS 10.15 ("Catalina") or higher
Why doesn't Chrome as a second factor work on my iMac?
For devices older than 2021, 2FA registration only works with Safari, no other browser.
Why is that?
The Chrome browser needs access to a biometric sensor. The older iMacs do not have this. Chrome only works on the iMac (as of May 2021) with M1 processor.
What needs to be done to register with the Safari browser?
The following requirements must be met:
- macOS 11 (or newer) with current patch level is installed.
- AppleID is used.
- Keychain in the cloud is used.
Linux devices
Why are there no instructions for Linux devices?
Linux devices do not yet support the device-based registration process for two-factor authentication (2FA).
If you have a Linux device, please use an additional device for authentication, such as a smartphone or FIDO stick.
Another alternative is to use a passkey. However, this functionality may not be available in the context of every Linux distribution:
Option 1 - Chrome browser with a registered Google account
If you use the Google Chrome browser on your Linux-based device and have registered and signed into a Google account on it, you can select ‘this device’ during the registration process: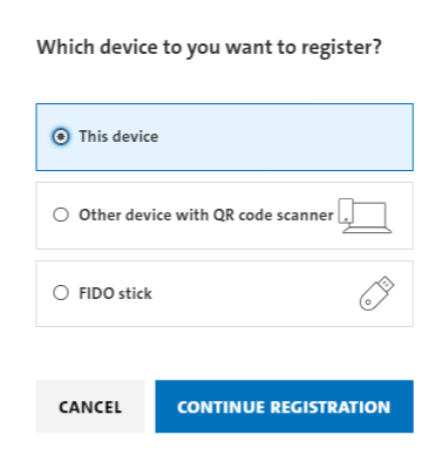
After that, please follow the instructions generated by the browser to create a passkey. If successful, the passkey can then be used in the Chrome browser as a second factor.
Option 2 - Creating and storing a ‘passkey’ in a password manager
Another option is to use an open-source password manager such as ‘KeePassXC’, in which a generated ‘Passkey’ is stored. Please follow these instructions (only available in German)
FIDO sticks
What is a FIDO stick or YubiKey?
FIDO2 is a new method for registering and logging in to web services. It can be used either instead of a password or as a second factor. To do this, you need an authenticator, which is available, for example, in the form of a USB stick that you can attach to your key ring.
When you log in, you simply insert the stick into the computer and press the button on the stick to authenticate yourself to the service. On Windows, Android and, to a limited extent, macOS, this even works without additional hardware, since the operating systems themselves act as virtual authenticators.
Depending on how the service has implemented FIDO2, the stick is sufficient for logging in (one-factor authentication) or you also have to enter a PIN or password (two-factor). Both variants are considerably more secure than relying on the password alone. YubiKey is a stick family from the manufacturer Yubico.
Can I get a FIDO stick?
If you are an employee:r of UHH and neither your computer (e.g. with Linux operating system) nor your cell phone can be configured as a second factor, you can order a FIDO stick in the RRZ-ServicePortal (to access the RRZ-ServicePortal e.g. from your home office, you first have to establish a VPN connection to the university network (if you do not use a terminal device managed by the RRZ). You can find more information about this here).
Does the Fido stick also work on an unknown computer?
In principle, yes. However, depending on the model, the installation of a device driver may be required to use a FIDO2 stick.
What do I do with the Fido stick when I leave the UHH?
The FIDO2 stick is a technical device provided to you that, like all other technical equipment, will be returned to the issuing office if you leave the UHH. Therefore, please send the FIDO2 stick with internal mail to the Regional Computing Center, stating your user ID:
Regional Computer Center
RRZ Service Desk
Schlüterstrasse 70
20146 Hamburg
Alternatively, you can return the FIDO2 stick to one of our RRZ Service Desk locations.
What do I do if I have forgotten the pin of the Fido stick?
With Windows operating system
If you have forgotten the PIN of the Fido stick, you must reset it. This is done in the "Logon options" in the "Settings" of Windows. In the "Security key" section, click on "Manage" and then on "Reset".
It may also be necessary to re-register the stick for 2FA.
With macOS operating system
Please install the "Yubico Authenticator" app from the Apple Store. You can use this app to reset the stick. You can do this in the app at the top right behind the button with the sliders. It may also be necessary to re-register the stick for 2FA.
With Linux operating system
Please use the program "Yubikey Manager", which is available here:
https://www.yubico.com/support/download/yubikey-manager/
If "pcsd" is installed, you only need to start the file and then you can choose whether you only want to use the program or install it.
